 Today, we’re going to go through the HackTheBox Sherlock (Blue Team) room called SmartyPants. It is a retired Sherlock and you can follow along for free here. There is also a blog post that HTB put out at the same time that talks about how to use SmartScreen logs, which is the core of what we have to do in this room. It is definitely worth reading, because it has a lot of good information not only on how SmartScreen works (and how to enable it), but how to use it from a forensic standpoint.
Today, we’re going to go through the HackTheBox Sherlock (Blue Team) room called SmartyPants. It is a retired Sherlock and you can follow along for free here. There is also a blog post that HTB put out at the same time that talks about how to use SmartScreen logs, which is the core of what we have to do in this room. It is definitely worth reading, because it has a lot of good information not only on how SmartScreen works (and how to enable it), but how to use it from a forensic standpoint.
Turning back to our activity, here’s the scenario:
Forela's CTO, Dutch, stores important files on a separate Windows system because the domain environment at Forela is frequently breached due to its exposure across various industries. On 24 January 2025, our worst fears were realised when an intruder accessed the fileserver, installed utilities to aid their actions, stole critical files, and then deleted them, rendering them unrecoverable. The team was immediately informed of the extortion attempt by the intruders, who are now demanding money. While our legal team addresses the situation, we must quickly perform triage to assess the incident's extent. Note from the manager: We enabled SmartScreen Debug Logs across all our machines for enhanced visibility a few days ago, following a security research recommendation. These logs can provide quick insights, so ensure they are utilised.
To kick it off, we have to download a 4MB zip file called SmartyPants.zip. It is password protected and – as usual – the password is hacktheblue. Inside, there is a folder called Logs and that folder contains 358 .evtx (Windows Event Viewer) files. There are ways to do this with Linux, including multiple utilities that convert .evtx to JSON or CSV. I’m going to just tackle this with Windows.
Task 1: The attacker logged in to the machine where Dutch saves critical files, via RDP on 24th January 2025. Please determine the timestamp of this login.
Let’s open up the Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx file. It has 33 events in it and I want to filter for Event ID 1149, which represents “Remote Desktop Services: User authentication succeeded”. So I select the Action Filter Current Log… and enter 1149 for the Event ID and click OK. There is literally only one.
Remote Desktop Services: User authentication succeeded:
User: Dutch
Domain:
Source Network Address: 0:0:fe80::d18c:695%1989170785
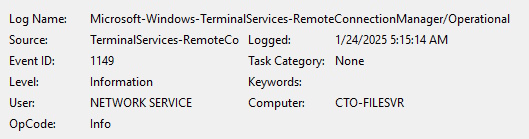
You’ll notice that the user is Dutch and we have our timestamp. However, in this view, it is adjusted for my local time, which is Eastern Daylight Time (currently GMT – 500). If we switch the Event Viewer and look at the XML view, it does show the original time before Windows tried to “help” me.
<TimeCreated SystemTime="2025-01-24T10:15:14.4560120Z" />
Task 1 Answer: 2025-01-24 10:15:14
Task 2: The attacker downloaded a few utilities that aided them for their sabotage and extortion operation. What was the first tool they downloaded and installed?
This time, we want to dig into the Microsoft-Windows-SmartScreen%4Debug.evtx file to see what they were doing. We know they logged on at 5:15AM (my time), which is about when this log starts. So I want to look at earlier events (bottom of my default sort) and not the later ones that are at the top. I clicked through and saw where the user opened MS Edge (which went through a few checks) and then downloaded a file that was also SmartScreen checked.
{"$type":"isFileSupported","executionTime":"9281","path":"C:\\Users\\Dutch\\Downloads\\winrar-x64-701.exe","size":"3912088"}
Task 2 Answer: WinRAR
Task 3: They then proceeded to download and then execute the portable version of a tool that could be used to search for files on the machine quickly and efficiently. What was the full path of the executable?
Same deal here. Stay in the same log and just follow what the user was doing in the browser. It is only a few more log entries above this last one.
{"$type":"isFileSupported","executionTime":"8701","path":"C:\\Users\\Dutch\\Downloads\\Everything.exe","size":"1778192"}
Note that the double slashes are just the tool escaping the slashes. The correct answer only has single backslashes throughout. Also, I’ve seen some complaints in the reviews of this room on HTB where people were upset and didn’t know when to say the tool and when to say the path. Pay very close attention to the question and the preview hints in the textboxes. I don’t know if they’ve updated them since the room was released, but the current version of both is pretty clear.
Task 3 Answer: c:\Users\Dutch\Downloads\Everything.exe
Task 4: What is the execution time of the tool from task 3?
Same log, just keep traversing up / forward in time. Here are the relevant parts of the XML view (so timezone is correct).
<TimeCreated SystemTime="2025-01-24T10:17:33.5613231Z" />
<Data Name="Data">{"$type":"isFileSupported","executionTime":"8701","path":"C:\\Users\\Dutch\\Downloads\\Everything.exe","size":"1778192"}</Data>
Task 4 Answer: 2025-01-24 10:17:33
Task 5: The utility was used to search for critical and confidential documents stored on the host, which the attacker could steal and extort the victim. What was the first document that the attacker got their hands on and breached the confidentiality of that document?
Broken record. Same log, new few log items.
{"$type":"isFileSupported","executionTime":"3720","path":"C:\\Users\\Dutch\\Documents\\2025- Board of directors Documents\\Ministry Of Defense Audit.pdf","size":"2679956"}
Task 5 Answer: C:\Users\Dutch\Documents\2025- Board of directors Documents\Ministry Of Defense Audit.pdf
Task 6: Find the name and path of second stolen document as well.
19 seconds later.
{"$type":"isFileSupported","executionTime":"3726","path":"C:\\Users\\Dutch\\Documents\\2025- Board of directors Documents\\2025-BUDGET-ALLOCATION-CONFIDENTIAL.pdf","size":"523480"}
Task 6 Answer: C:\Users\Dutch\Documents\2025- Board of directors Documents\2025-BUDGET-ALLOCATION-CONFIDENTIAL.pdf
Task 7: The attacker installed a Cloud utility as well to steal and exfiltrate the documents. What is name of the cloud utility?
Stay in the log and keep tracing their movements.
{"$type":"isFileSupported","executionTime":"12443","path":"C:\\Users\\Dutch\\Downloads\\MEGAsyncSetup64.exe","size":"78861432"}
Keep in mind, they asked for the name of the cloud utility not the path or file name. You can find it by intuition or googling that installer name.
Task 7 Answer: MEGAsync
Task 8: When was this utility executed?
You know the drill by now. We keep going and find when the next log entry that contains the execution. Here’s the relevant parts.
<TimeCreated SystemTime="2025-01-24T10:22:19.4792842Z" />
<Data Name="Data">{"$type":"isFileSupported","executionTime":"3675","path":"C:\\Users\\Dutch\\AppData\\Local\\MEGAsync\\MEGAsync.exe","size":"77568264"}</Data>
Task 8 Answer: 2025-01-24 10:22:19
Task 9: The Attacker also proceeded to destroy the data on the host so it is unrecoverable. What utility was used to achieve this?
Again, just asking for the name. Move on a little further and we get this.
{"$type":"isFileSupported","executionTime":"7943","path":"C:\\Users\\Dutch\\Downloads\\file_shredder_setup.exe","size":"2317839"}
Task 9 Answer: File Shredder
Task 10: The attacker cleared 2 important logs, thinking they covered all their tracks. When was the security log cleared?
We actually have to switch logs for this one. We have only used 3 of the 358 logs, but I guess HTB really wanted you to know not only HOW to look, but WHERE to look. They are asking about the Security log. Open that one, Security.evtx. Scroll to the very bottom (or wherever the earliest log is for you). The Task Category is “Log clear” and the XML has a section called LogFileCleared in the user data. Here are the relevant parts.
<TimeCreated SystemTime="2025-01-24T10:28:41.9338490Z" />
<LogFileCleared xmlns="http://manifests.microsoft.com/win/2004/08/windows/eventlog">
<SubjectUserSid>S-1-5-21-3088055692-629932344-1786574096-1003</SubjectUserSid>
<SubjectUserName>Dutch</SubjectUserName>
<SubjectDomainName>CTO-FILESVR</SubjectDomainName>
<SubjectLogonId>0xe1d52</SubjectLogonId>
</LogFileCleared>
Task 10 Answer: 2025-01-24 10:28:41
That’s it. Not too bad. Maybe it would have been more exciting if I wrestled with some of the Linux-based tools, but – personally – when I’m administering a Windows environment, I definitely have a Windows machine (at least a VM), so this was better practice to learn about SmartScreen. If you did it differently, comment a link to your blog post, writeup, or video and I’ll definitely check it out!
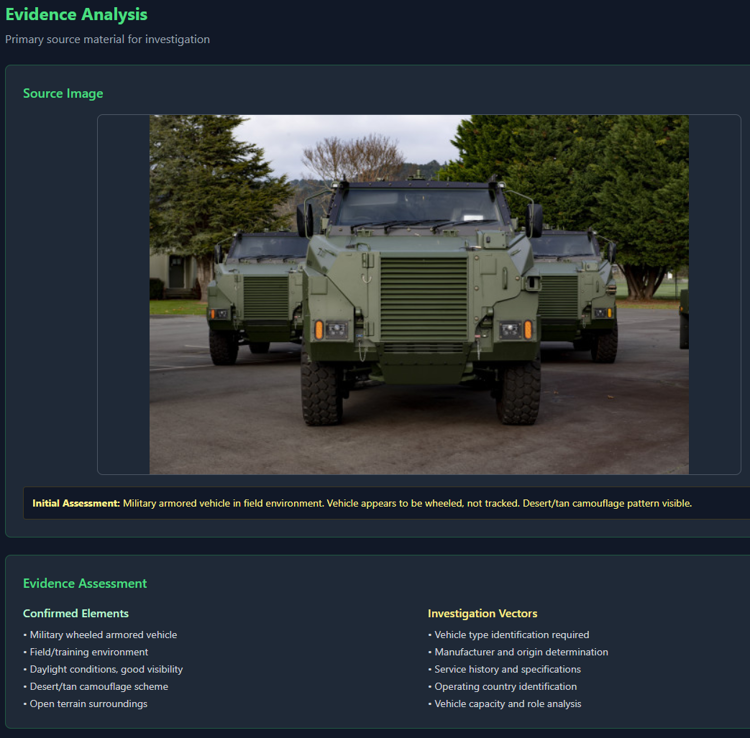
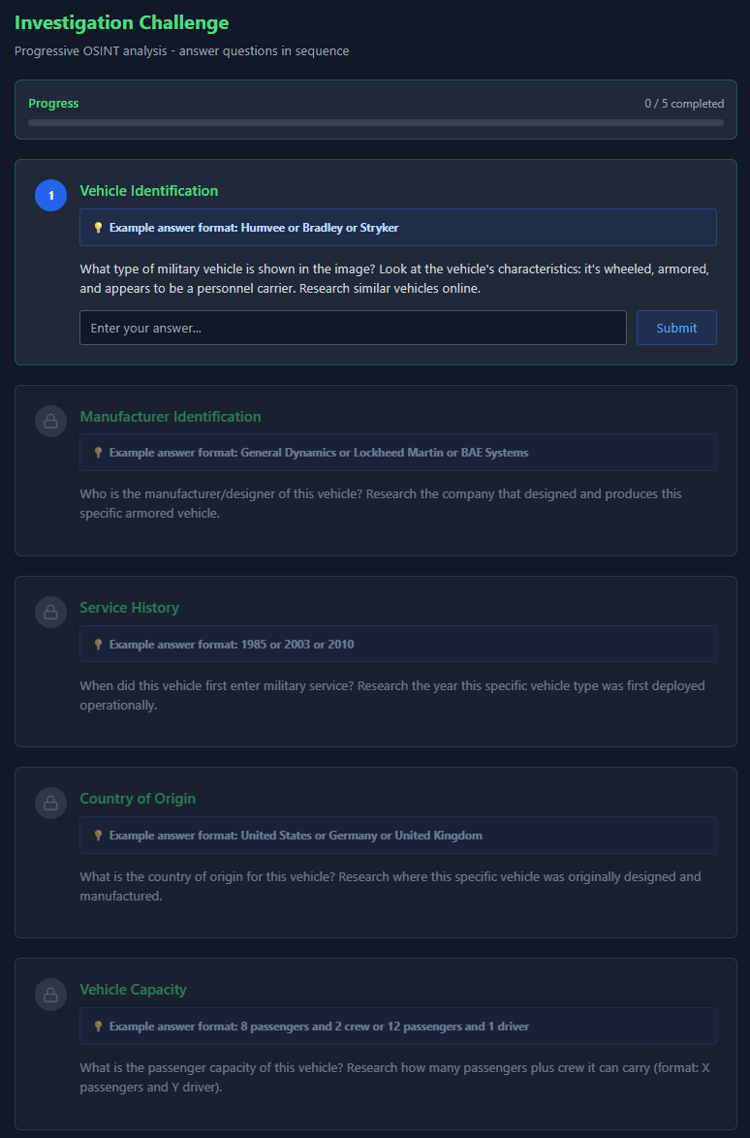

 Today’s challenge is a very easy challenge from Hack the Box. You can find it
Today’s challenge is a very easy challenge from Hack the Box. You can find it 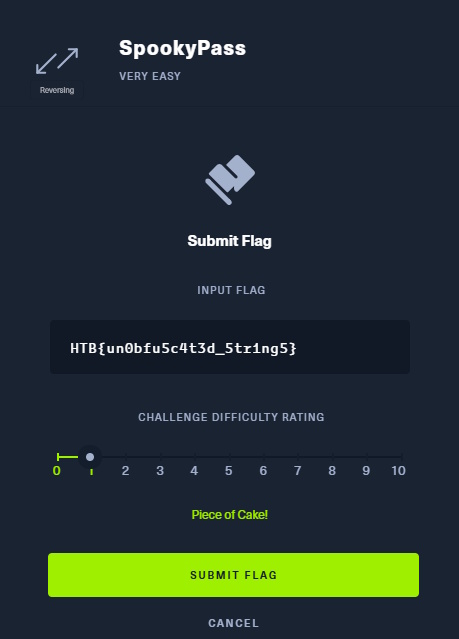

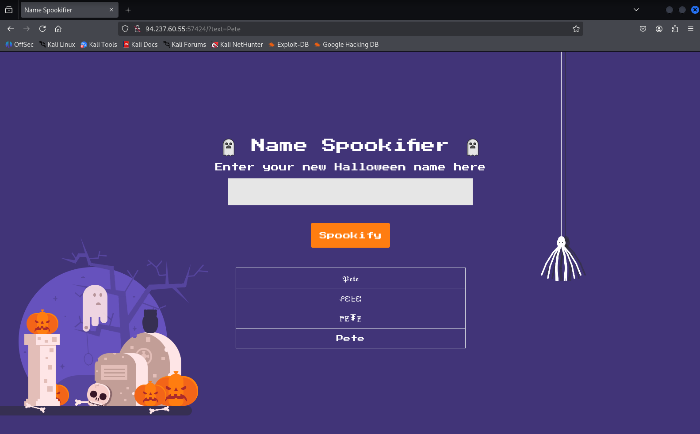
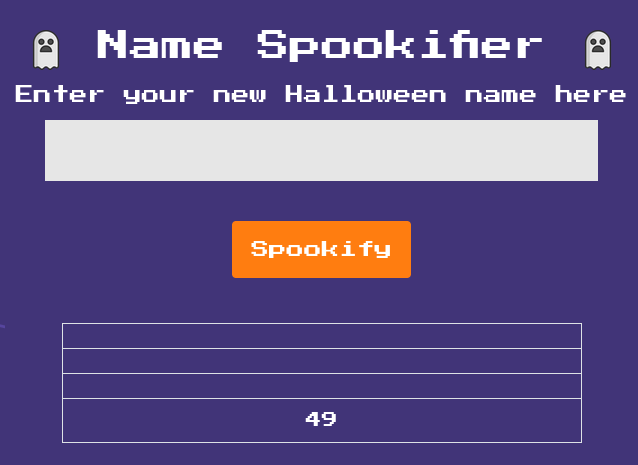
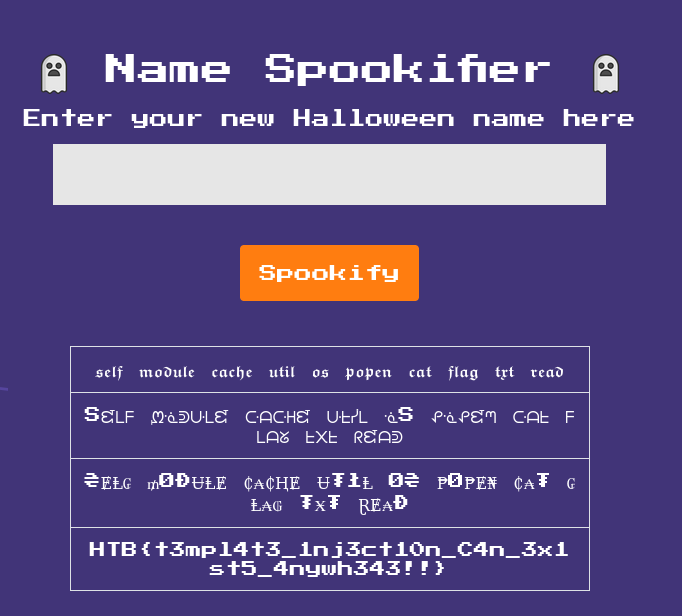
 Today, we’re going to take on a Hack the Box challenge called Spookifier. This is a free, retired challenge that you can find
Today, we’re going to take on a Hack the Box challenge called Spookifier. This is a free, retired challenge that you can find 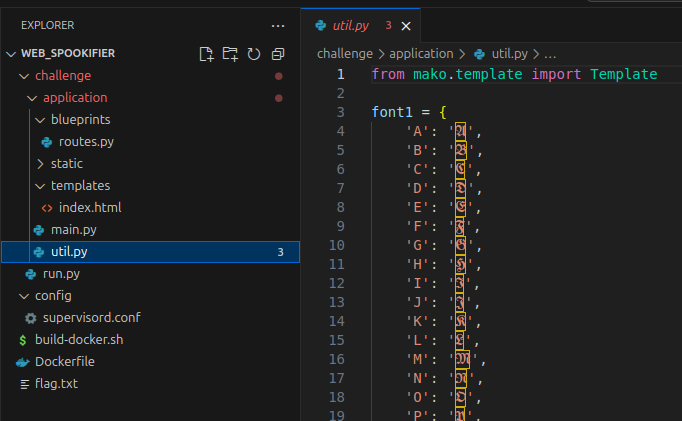

 Today, we’re going to go through the HackTheBox Sherlock (Blue Team) room called SmartyPants. It is a retired Sherlock and you can follow along for free
Today, we’re going to go through the HackTheBox Sherlock (Blue Team) room called SmartyPants. It is a retired Sherlock and you can follow along for free 
