 Our capture the flag walkthrough today is found over on Hack the Box (HTB). Instead of the offensive security walkthroughs that I’ve been doing, this one is more focused on defensive investigative skills. These classifications for these rooms at HTB are called “Sherlocks” and today’s room is a retired free one called Dream Job-1. It focuses on researching a specific attack campaign, the attackers, and their tactics. Let’s get started.
Our capture the flag walkthrough today is found over on Hack the Box (HTB). Instead of the offensive security walkthroughs that I’ve been doing, this one is more focused on defensive investigative skills. These classifications for these rooms at HTB are called “Sherlocks” and today’s room is a retired free one called Dream Job-1. It focuses on researching a specific attack campaign, the attackers, and their tactics. Let’s get started.
The first thing we have to do is download the attached zip file called DreamJob1.zip. They give you the password to extract it as hacktheblue. Inside the zip is one file named IOCs.txt containing 3 lines of text. For now, we won’t need this file until Question 10.
Task 1: Who Conducted Operation Dream Job?
So unlike TryHackMe, Hack the Box doesn’t really teach you how to do things. You either have to know how, have worked through some of their training elsewhere, have access to walkthroughs, or be good at searching. In this case, we’re going to go to the MITRE ATT&CK® homepage at https://attack.mitre.org/. Click on CTI then Campaigns.
Scroll down until you get to C0022 Operation Dream Job or Ctrl-F and search for Operation Dream Job on the page.

Task 1 Answer: Lazarus Group
Task 2: When was this operation first observed?
Click the name or ID of the campaign and it takes you here: https://attack.mitre.org/campaigns/C0022/. You can see in the Info Box on the right some quick info about this campaign, including when it was First Seen.
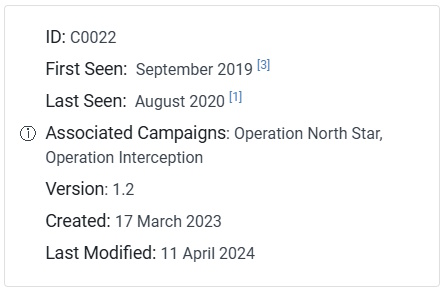
Task 2 Answer: September 2019
Task 3: There are 2 campaigns associated with Operation Dream Job. One is Operation North Star, what is the other?
Using the same image, we can see the Associated Campaigns.
Task 3 Answer: Operation Interception
Task 4: During Operation Dream Job, there were the two system binaries used for proxy execution. One was Regsvr32, what was the other?
Scroll down or search for Binary Proxy Execution. You can see the two mentioned, the answer is the other one.
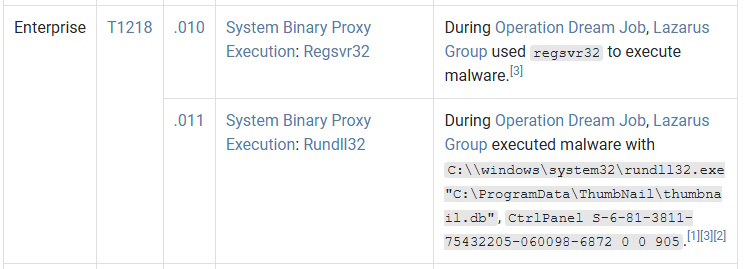
Task 4 Answer: Rundll32
Task 5: What lateral movement technique did the adversary use?
On the page, near the top, you can click into the ATT&CK® Navigator Layers dropdown and View.
After you get to the layers, horizontally scroll right until you see Lateral Movement. Click the header to have the column highlighted (can be a bit cramped and this helps to see).
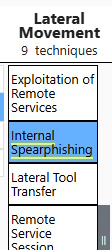
Task 5 Answer: Internal Spearphishing
Task 6: What is the technique ID for the previous answer?
Hover/Click on that highlighted part and read the kick out.
Task 6 Answer: T1534
Task 7: What Remote Access Trojan did the Lazarus Group use in Operation Dream Job?
Go back to the Operation Dream Job Campaign Page. Scroll down to Software.
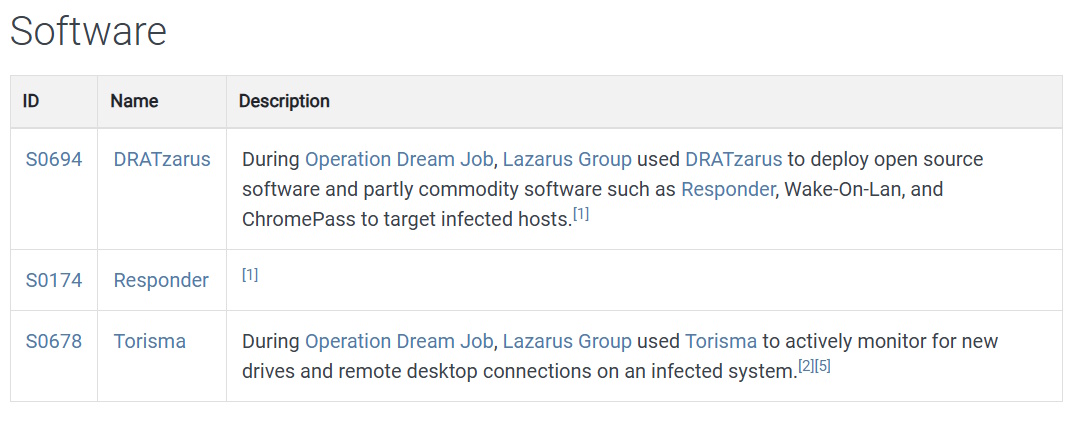
Task 7 Answer: DRATzarus
Task 8: What technique did the malware use for execution?
Click the Software Link for DRATzarus and go to https://attack.mitre.org/software/S0694/
Use the Navigator Layers dropdown like we did before and load up its Enterprise Layer and go to Execution. Native API is highlighted.
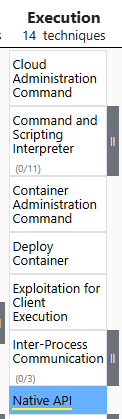
Task 8 Answer: Native API
Task 9: What technique did the malware use to avoid detection in a sandbox?
On the same page, under Discovery, there is a box called Virtualization/Sandbox Evasion. Its child box has the answer.
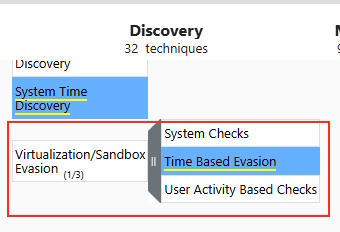
Task 9 Answer: Time Based Evasion
Task 10: To answer the remaining questions, utilize VirusTotal and refer to the IOCs.txt file. What is the name associated with the first hash provided in the IOC file?
Looking in the file, the first hash is 7bb93be636b332d0a142ff11aedb5bf0ff56deabba3aa02520c85bd99258406f
If we go to VirusTotal and put in that hash, it takes us here
After you search, it takes you to the page and the answer is right in the header.
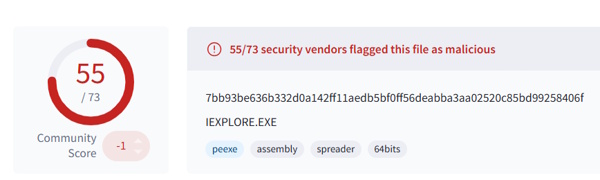
Task 10 Answer: IEXPLORE.EXE
Task 11: When was the file associated with the second hash in the IOC first created?
Second hash from the file is adce894e3ce69c9822da57196707c7a15acee11319ccc963b84d83c23c3ea802. If we search it, it takes us here.
Details -> History -> Creation Time
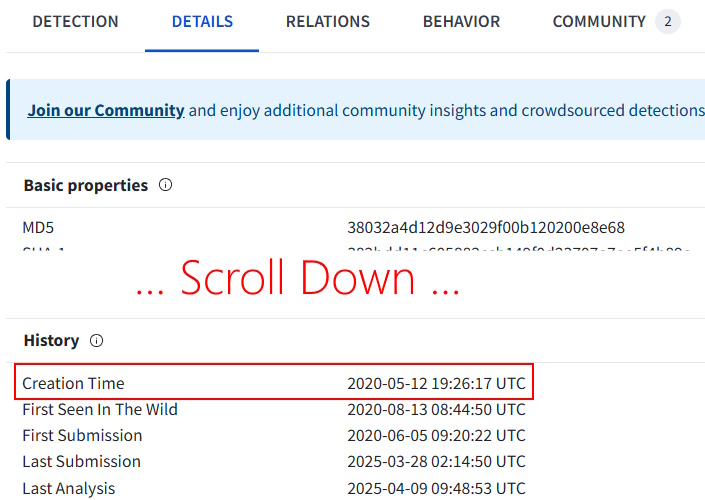
Task 11 Answer: 2020-05-12 19:26:17
Task 12: What is the name of the parent execution file associated with the second hash in the IOC?
Same page, Relations -> Execution Parents
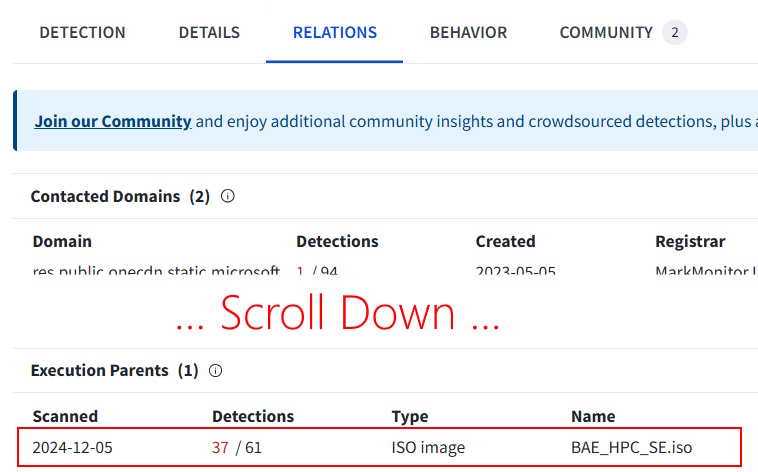
Task 12 Answer: BAE_HPC_SE.iso
Task 13: Examine the third hash provided. What is the file name likely used in the campaign that aligns with the adversary’s known tactics?
Third hash from the file is 0160375e19e606d06f672be6e43f70fa70093d2a30031affd2929a5c446d07c1. If we search it, it takes us here.
Go to Details -> Names
Remember that according to the task, the victims of this were job seekers and that they used “fake job lures”, so…
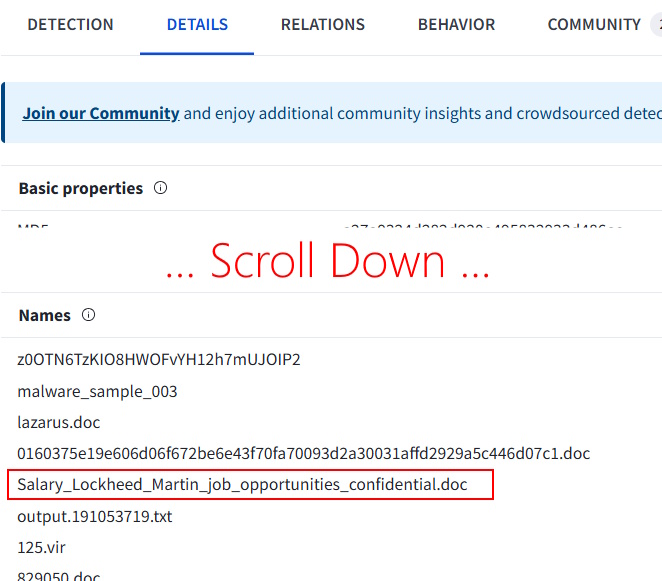
Task 13 Answer: Salary_Lockheed_Martin_job_opportunities_confidential.doc
Task 14: Which URL was contacted on 2022-08-03 by the file associated with the third hash in the IOC file?
Relations -> Contacted URLs, look for Scanned = 2022-08-03
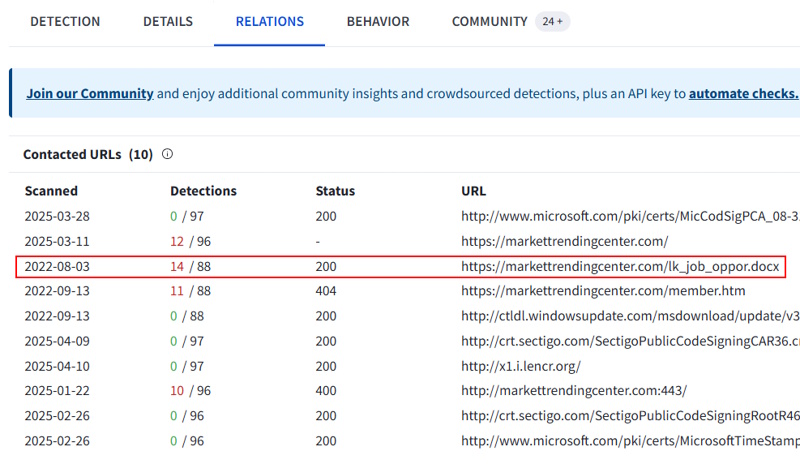
Task 14 Answer: https://markettrendingcenter.com/lk_job_oppor.docx
That’s it. I hope you enjoyed this little Blue Team exercise in researching some details of an attack from some artifacts!